奈良先端科学技術大学院大学 情報セキュリティ工学研究室
ISE Lab Activities

Students with a variety of backgrounds join the ISE Lab. They spend approximately six months after entering the school learning the skills that we require to conduct research.
First, students learn the skills needed to obtain secret keys using side-channel information leaked from encryption modules through round-table discussions and exercises. Then, as additional skills required to conduct research in other areas are largely the same, students acquire this knowledge also through round-table discussions and exercises.
Programming skills
Programming is an essential skill for our students regardless of the research topic. The training to program the processes that students want to conduct takes place through round-table discussions. Although the problems are puzzle-like and simple, in many cases, it will be challenging to arrive at a solution if there is no awareness of data structure and algorithms. At the end of this training, the participants can easily write down the programs corresponding to the processes they envision.
Hardware programming for implementation of cryptographic algorithms
In computation, hardware processing is often more efficient. During a series of exercises, students perform common key encryption (e.g., AES) and public key encryption (e.g., RSA) hardware implementations to acquire necessary hardware programming skills and confirm the effectiveness of hardware processing.
Measurement of side-channel information
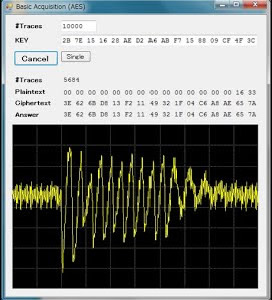
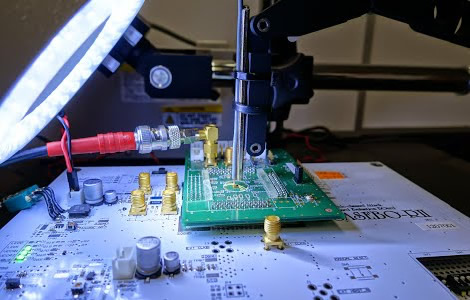
Hardware security research is broadly divided into measurement and analysis, with this series of exercises being focused on measurement. In previous exercises, participants measure the AES installed on circuits, and subsequently, leaked side-channel information is measured. These activities allow students to gain skills concerning the selection and operation of measurement devices suited to information leaks, and the selection and usage methods for probes, amplifiers, and filters. They also learn about the mechanisms of information leakage during circuit operation.

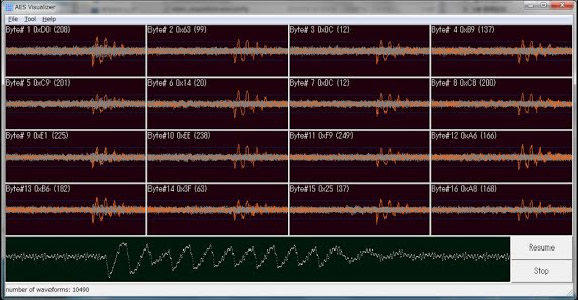
Secret key analysis based on observation of side-channel information
During these analytical exercises, students extract secret keys using side-channel information leaked from encryption modules by fusing the acquired software and hardware programming experience with the knowledge on measurement methods. Given that factors such as the quality of side-channel-information measurement and model compatibility have a great impact on key extraction, the participants learn about efficient secret key extraction and modification of these factors when appropriate.